Tingkatkan Pelanggan
untuk menjadi yang Terbaik
Tingkatkan
Pelanggan untuk menjadi yang Terbaik
Transformasi bisnis dengan aplikasi loyalty program dari Bliss.
Powered by ![]()
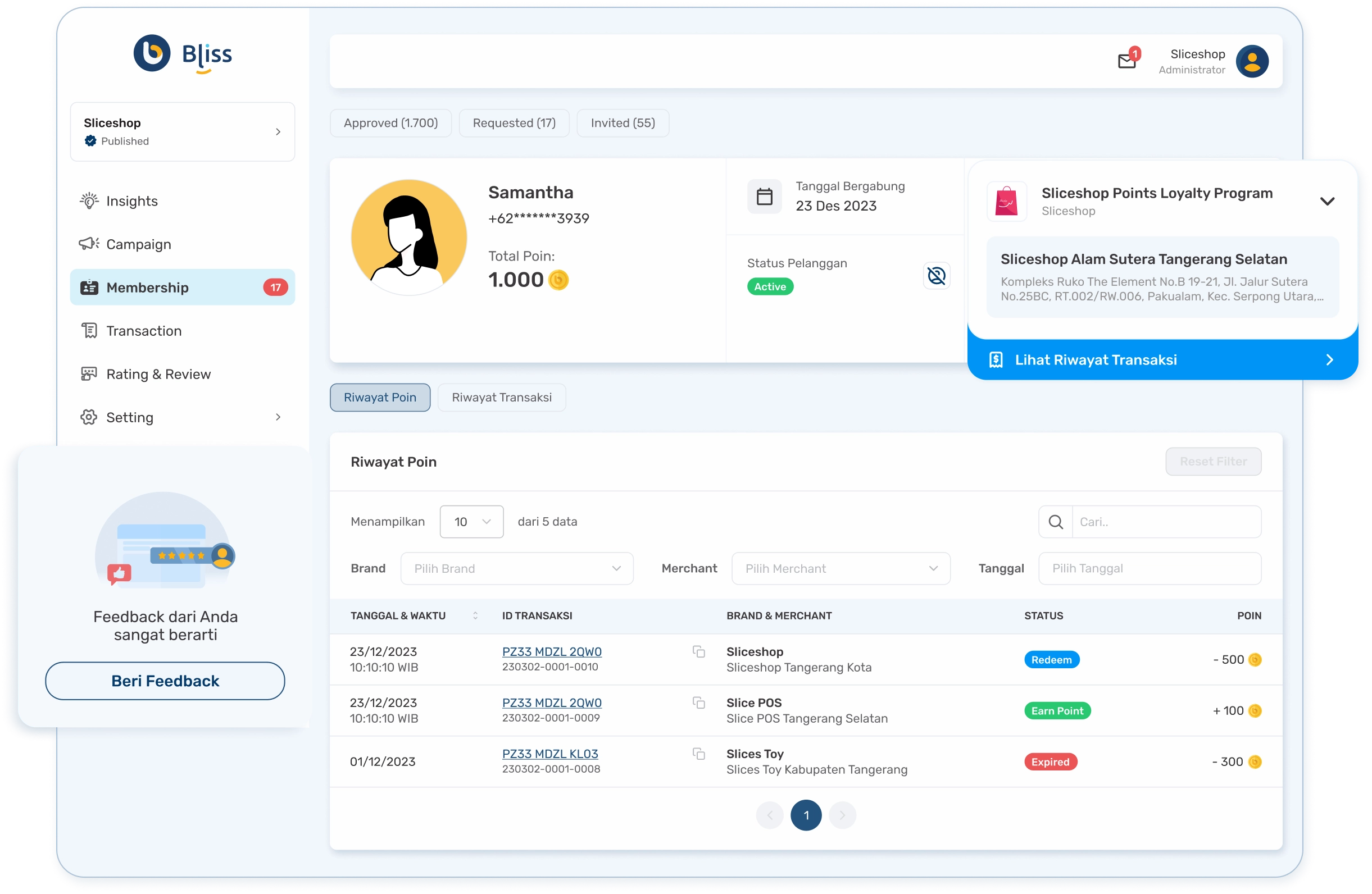

Siap bikin pelangganmu ketagihan belanja?

Bliss Loyalty Program
Memudahkan pebisnis mengelola membership digital untuk meningkatkan loyalitas, retensi, dan kepuasan pelanggan.

Loyalty Program
Kelola loyalty program untuk seluruh brand Anda dengan mudah dalam satu platform terintegrasi.
Poin Reward
Atur ketentuan perolehan dan penukaran poin reward untuk setiap transaksi dari member Anda.
Promo Message
Tingkatkan penjualan dengan mengirim pesan promosi kepada member Anda dengan kriteria tertentu.
Perluas Jangkauan Pasar
Tidak hanya meningkatkan loyalitas, retensi, dan kepuasan pelanggan, Bliss membantu Anda menjangkau lebih banyak konsumen baru.


Kemudahan Bliss untuk Bisnismu

Terintegrasi dengan Semua
Produk Accurate
Bisnis Anda menjadi lebih optimal karena terhubung secara sinergis dengan seluruh produk Accurate.
Sinkronisasi data lebih baik
Fleksibilitas penggunaan
Pembuatan laporan lebih mudah

Targeted & Blasting Campaign
Personalisasi mendalam dan maksimal
Segmentasi audiens secara presisi
Analisis data akurat

Bergabung dengan Bliss Sekarang
Jalin hubungan yang lebih baik dengan pelanggan Anda, tingkatkan kesuksesan dan keuntungan pada bisnis Anda
